Good morning everyone!
One shot secret function…. I’m hearing you saying… what?
To talk about this function I have to talk about a nice website I discovered in the past days. The site is the following:
In this site you can find some online encryption services, as the following:
- encrypt a text message
- encrypt a file (of course, you have to upload the file!)
- generate a password
- share a one shot secret
I believe that the most interesting is the last one… Let’s see how it works.
Suppose you have this need: you need to communicate to someone the credentials to access to a certain online service. You could use, for example, a simple email, but there are some drawbacks:
- the message could be intercepted
- the message could be read by other people that may have access to your email or to recipient’s email
- if you forget to delete the message, it will remain in your inbox and still be read by other people
The “One shot secret” function can, to some extent, solve these problems.
Click on the link “One shot secret” to reach the page in which you can use the service. You will see the following page:
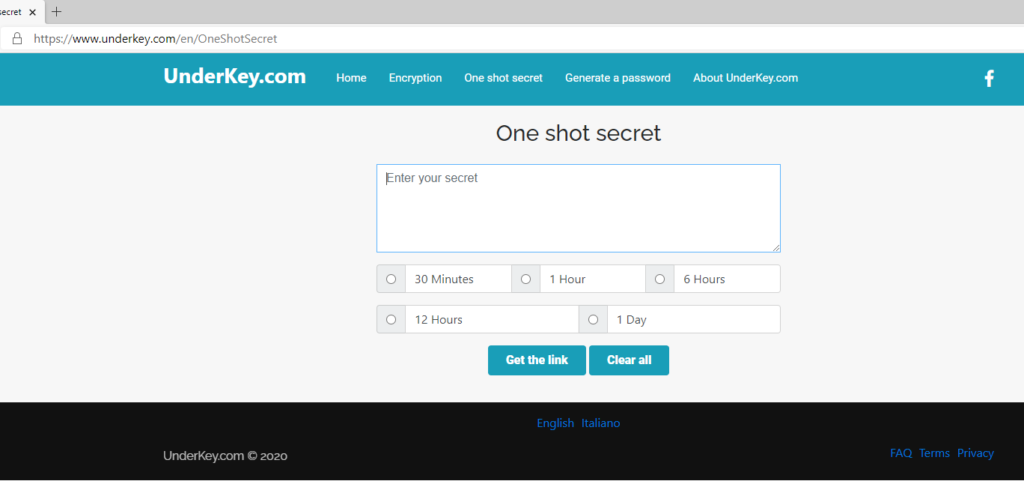
Now enter your secret and choose the option to indicate how long you want to keep the stored message. I configured the page as follow:
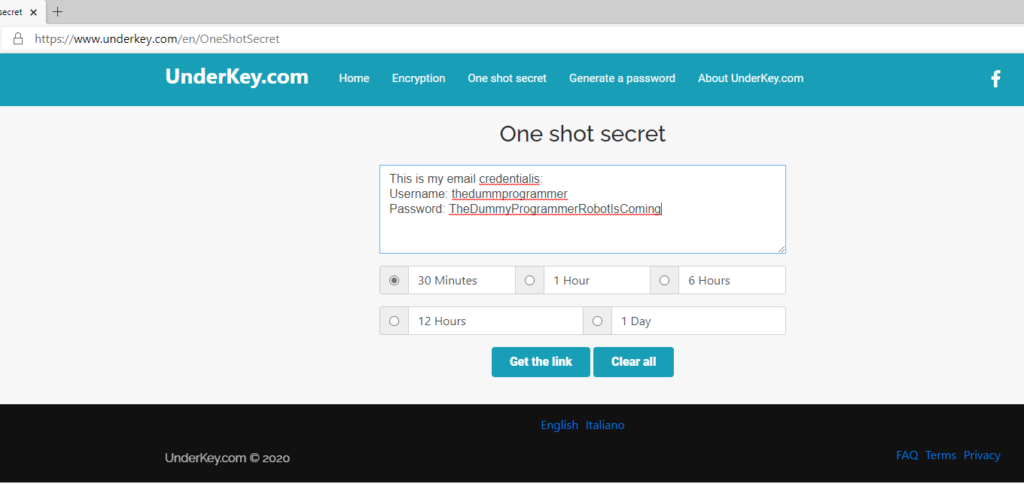
Click on the “Get the link” button. A link to read the message will be shown, as you can see in the following screenshot:
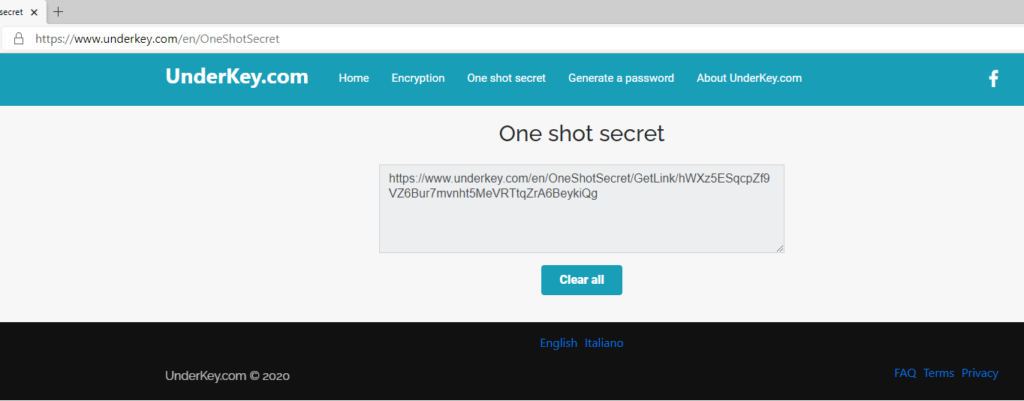
Now you can send the link to your recipient, using for example an email.
In this way you have these advantages:
- the message is deleted immediately the first time the link is accessed, so you can detect if someone other than the correct recipient has accessed, because the recipient will not be able to read the message
- UnderKey.com is under https, so your communication while reading the message is encrypted
- If the recipient forget to delete the email, the secret message is no more accessible because the link is no more valid
Have a nice day!